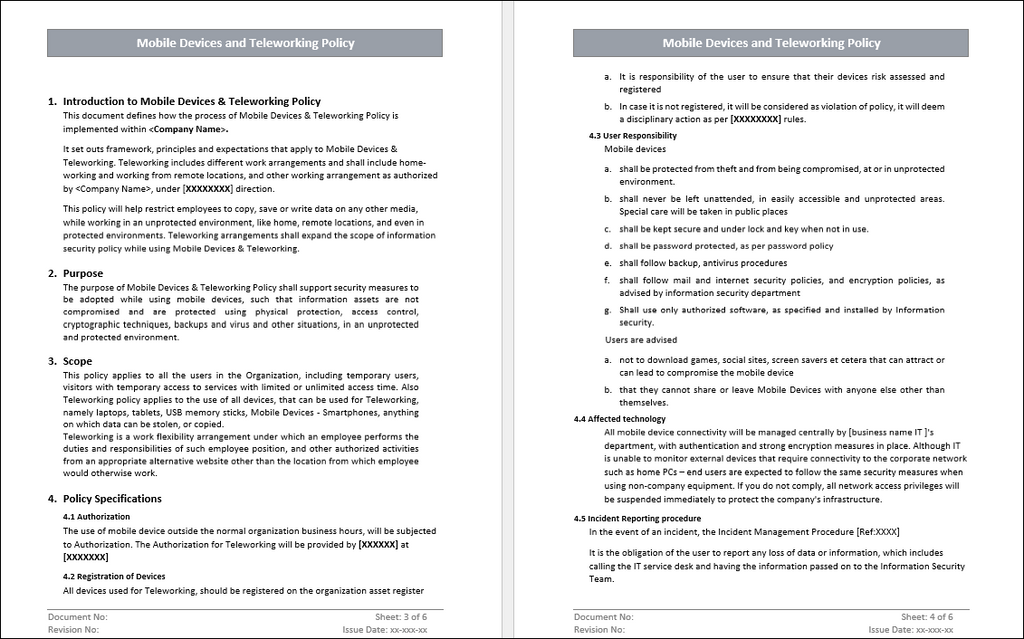
ISO 27001 Mobile Device And Teleworking Policy Template
Introduction
On the one hand, modern workplaces are increasingly depending heavily on mobile devices and teleworking, but one the other hand, it increases efficiency and productivity while on the other introduces new security dangers. ISO 27001 mobile device policy, paired with teleworking or remote-working policy, is all organizations must have to manage those risks.. ISO 27001 Annex A requires a mobile device policy (Control A.6.2.1) and a teleworking policy (Control A.6.2.2) to secure devices and data outside the office, and indeed, it is quite clear about these two requirements. A good policy, though, will protect corporate information on smartphones, laptops, and tablets when an employee is offsite. Proper policies ensure that the data is encrypted, the devices are managed, and that employees comply by security rules. As one expert guide notes, such a policy "is used to manage the risks introduced by usage of mobile devices and protects information accessed at teleworking sites."
Why An ISO 27001 Mobile Device Policy Is Important
In the past years, remote access and work through mobile devices grew greatly, making the value and need for security policies greater. If a device is lost or compromised, it usually exposes sensitive data. An example of uncontrolled teleworking is such that it is "most vulnerable to hacking, malware, unauthorized access, etc." An effective policy prescribes mandatory controls which mitigate these risks directly.
-
Protecting Sensitive Data- A mobile device would store confidential information. The policy must require strong device security (PINs, encryption) in order that if a phone is stolen, it will not expose the company's data. For example, ISO guidance includes cryptography and PINs/passwords on devices and enabling remote lock or erasure if a device is lost.
-
Control Device Usage- BYOD and personal use of mobile devices create risks. A policy specifies what is permitted-e.g. forbidding illegal downloads or unlicensed apps on work devices. By forbidding high-risk actions (like accessing malware sites or using personal devices with unauthorized work apps), the policy covers a large range of attack vectors.
-
Compliance- ISO 27001 requires these policies. Furthermore, it aids audits as well as certification. It makes employees responsible (employees usually must accept this, perhaps through an employee declaration). Regular backups, approved software, and clearly defined incident-reporting processes are included in this model form of practice. As one toolkit notes, templates typically have device management and incident reporting sections to cover these.
Critical Aspects of ISO 27001 Mobile Device Policy
An effective mobile device policy should define how to safeguard, use and maintain a device. A few key clauses typically cover the following subjects:
-
Device Registration and Ownership: All corporate mobile devices (and approved personal devices, if BYOD is allowed) must be recorded in an asset register and assigned to a responsible owner. This ensures each device is tracked. For example, policy might state that "mobile devices are recorded in the asset register and assigned to a named individual," and that owners are given a copy of the policy and their responsibilities.
-
Access Controls (PIN/Password & Encryption): The policy should require all devices to have strong authentication (PIN, password, biometric) and full-disk encryption protecting work data. ISO guidance explicitly recommends "secret authentication, such as passwords and PINs," and notes encryption as a key measure. Furthermore, requiring lock screens and auto-lock timeouts is intended to secure devices if unattended.
-
Restricting Software and Applications: The policy forbids installation of unapproved applications or unlicensed software on corporate devices to prevent the probability of malware. For example, it may state that "employees must not use their mobile devices for illegal or prohibited activities," such as installing pirated apps or visiting unsafe websites. Also, only the company-approved software and updates may be used with patch management procedures (regular OS/app updates) enforced to fix vulnerabilities.
-
Mobile Device Configuration (Firewall/Antivirus): Guidelines usually require personal firewalls or antivirus on devices, particularly those accessing critical environments. For instance, one policy excerpt dictates that a personal firewall configured appropriately should be on any mobile device that accesses payment networks. Generally, organizations should ensure that devices run the most current up-to-date anti-malware and firewall settings as part of the security controls of the policy.
-
Backup & Recovery of Data: The policy should define backup requirements for mobile data. It might say that "mobile devices must take regular backup of work data to a secure server or cloud storage'' and provide recovery procedures to deal with any lost or damaged devices. Regular backup reduces data loss in the case of device failure. (Certain policies devolve partial responsibility for some uploads onto users, though still under oversight.)
-
Procedures for Lost/Stolen Devices: Coverage for a mobile policy that discusses lost devices is critical. For example, an employee should be required to report any lost or stolen device immediately, and such a policy should include provisions for remote wipe or lockout capabilities so that if a device "carrying sensitive information" is stolen or lost, it would be able to have its data erased. This is consistent with ISO's recommendation of applying remote lock/erase.
-
Acceptable Use and Communication: Many policies usually have a part of acceptable use. For instance, employees are usually allowed to use devices for work tasks (email, calls, etc.) but all communication must be professional; private use may be limited as not for personal social media or illegal downloads. One clause example states that "all work-related communication must be professional and adhere to the same standards as company-issued equipment." These rules prevent misuse of devices during work time.
-
Privacy and Personal Data: User privacy must also be part of the policy. For example, this specification can indicate that monitoring will take place only concerning corporate information and that sensitive personal info (health data, for instance) will not be collected unless authorized.
Basic Principle For A Teleworking Policy As Per ISO 27001
A remote working teleworking policy provides clear guidelines to employees about the mode of execution of their work outside office. Most teleworking policies have the following clauses:
-
Definition of Telework Approvals and Eligibility . The policy needs to state who can telework and under what conditions. It is usually phrased as "employees are permitted to telework on an as-needed basis, provided prior approval is obtained from their supervisor". This allows for only approved staff to work remotely. It might include performance requirements (e.g. telework not affecting instructional duties). Some templates link telework eligibility to job roles or successful completion of security training.
-
Work Schedule and Availability- Telework employees should adhere to the agreed schedules. One clause of the policy would be: "Employees are expected to adhere to their approved work schedule; any work outside the scheduled hours (emails, calls, etc.) requires prior approval." This will protect him from burnout and allow for supervision. Scheduled breaks and lunches will also be observed; normally the use of break time for work is not allowed without explicit authorization. Stating these hours clearly separates work from personal time.
-
Secure Workplace- There should be a requirement in policy regarding release of outside work in a secure place. Employees might be better require to be set up to work in a private locked space at home, away from family or visitors. Standards would address physical security (e.g. locked filing cabinets) and home office standards. Secure wifi is often required by the typical policy: it requires, for example, use of either company VPN or encrypted Wi-Fi in addition to public/open networks. According to notes from the ISO guidance, organizations should equip and then set rules to home communications equipment. This is very often spelled out in the items, saying that only company-approved networks and devices are allowed in.
-
Access Controls and Authentication- This is similar to the mobile policy with very strict authentication for remote access. In principle, it should require VPN support and multi-factor authentication (MFA) for any entry to the corporate system. It may go on to say in a policy, "employees must have the company network connect using VPN with 2-factor authentication," as proposed by ISO for endpoint security through using VPN and MFA. It is to avoid logins from home without proper authority.
-
Data Protection & Confidentiality- Teleworking means accessing the company's data remotely, thus putting a lot of emphasis on confidentiality in the policy. For instance, it may provide for password-locking and encrypting all home devices from unauthorized access, not very different from similar office specifications. Forbidding use of unapproved cloud services or personal email IDs for business data may be included in the clauses. One such clause reads, strimming employees "must take steps to protect all company information from unauthorized access or theft due to strong password using and approved apps." Effectively work from home should be as secure as the form of work set in the physical office.
-
Use of Company Equipment- Some would set up policy as to only use company-provided laptops or phones for work. If the company would allow the use of personal devices, broader sections would qualify such as all personal devices must meet all company security requirements (see BYOD notes below). The policy further provides any personal device used in the course of company work must be registered, approved, and kept updated.
-
Incident Reporting- The telework policy should include requirements to report any security incident or missing device without delay. E.g.: "Remote workers must immediately report any suspected data breach or loss of equipment to IT security." While ISO 27001 demands incident processes generally, this ensures immediate capture of any incidents occurring in remote locations. This could be mentioned next to mobile incidents (e.g. lost phone report).
- Disconnection and Return to Work- Most common is saying closing an employee opens to access (logging out of systems), returning all company-owned equipment once teleworking has ceased. Revocation of access rights will happen with termination of any teleworking privileges.

Common Components Of A Policy Template
A generic template for an ISO 27001 Mobile Device and Teleworking Policy would normally include:
1. Introduction/Purpose: Outlines the reason for the policy (ex: let it be heard that managing mobile/telework risks) and the value of security.
2. Scope: To indicate the employees, devices, and circumstances that fall within the boundaries of the policy. For example: "This policy applies to all company-issued and personal devices used for accessing corporate data."
3. Definitions: Clarifies key terms; mobile device, telework, device owner, etc.
4. Policy Statements (Specifications): These are in principle the essential clauses described above, such authentication requirements and acceptable use rules, as they apply to the conditions for teleworking. There may be subheadings to which these statements can be assigned, Mobile Device Security, Teleworking Security, BYOD Usage, etc.
5. Roles and Responsibilities: Who is responsible for what. This might list the VPN duty requiring IT, the employee's duty to report issues, and management's duty to approve telework. For example: device property must update and secure devices.
6. Awareness & Training: Demands training staff on the policy. ISO 27001 even mentions frequent awareness updates regarding teleworking controls.
7. Incident Reporting: How to report lost devices, breaches, or policy violations. (The policy should link to the main incident response process).
8. Policy Compliance/Non-Compliance: Describes how compliance will be checked (e.g. audits) and consequences for violations. For example, "non-compliance may result in loss of telework privileges and disciplinary action." So note the guidelines of ISO, which tell that compliance can be checked through audit and reports.
9. Exceptions: Processes for dealing with exceptions or special cases (e.g. temporary access for contractors).
10. Review and Updates: States that the policy will be reviewed periodically and updated as necessary, e.g., on new technology or following incidents.
11. Supporting Documents: References to related policies (like Access Control, Information Classification, Acceptable Use, etc.) or technical standards.
Best Practices in Policy Implementation
Writing policy is only the first thing. To ensure that it gains the desired effect, consider the following best practices:
-
Training & Awareness: Ensure training of all employees (including contractors) on the mobile/teleworking policy. ISO 27001 has requirements for ongoing awareness around controls applicable to remote work. For instance, include the policy in security orientation and hold periodic refreshers.
-
Enforcement Via Technology: Enforce technical requirements (e.g., push encryption keys, install antivirus, enforce PIN rules) via mobile device management (MDM) or enterprise mobility tools. This does automate compliance with the policy.
-
Periodic Review: In general, the policy should be reviewed and revised in line with changes in technology and organization practice. ISO guide notes that policies have to be regularly reviewed. For instance, if new mobile platforms or collaboration apps are adopted, then revise the rules.
-
Monitor & Audit: Random checks or internal audits can verify compliance, as suggested for ISO policies. Periodically audit configurations of devices and logs for reports on remote access in terms of compliance. Collect reports (e.g. on levels of patches or VPN usage).
-
Management Support: Such endorsements and support should be done at all levels of management to be seen as an organization that takes mobile and telework security seriously, thereby encouraging compliance from employees.
-
Incident Handling: With respect to remote working, there should be clear plans for incident response (e.g., lost phone, data breach while teleworking). These procedures should be tested so that issues are swiftly resolved.
With these practices, the ISO 27001 mobile device policy and teleworking policy remain living documents.
Conclusion
A globalized ISO 27001 mobile device teleworking policy is a necessity in today's flexible working environment. Clear policies such as mandatory device encryption, restrictions on use, and secure remote access reduce the risk of exposing an organization's information assets when employees work out of sight. The examples given indicate how to translate ISO 27001 requirements into practical clauses. Policy template may save time, but every institution should change it to match its needs. The ultimate goal of such a framework of policy is that it meets ISO 27001 standards while enabling mobility of productivity in organizations. That businesses can make the necessary provisions in regarding remote work without endangering data integrity and compliance is established with these mobile device security and telework controls.

