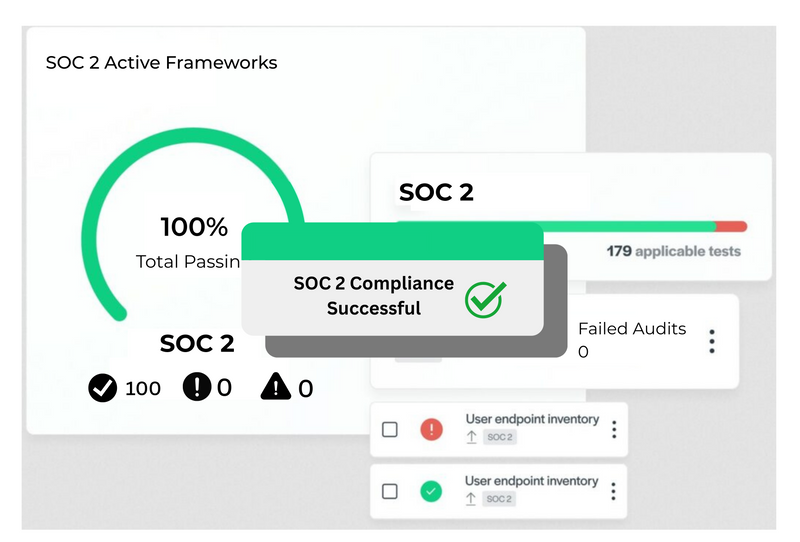
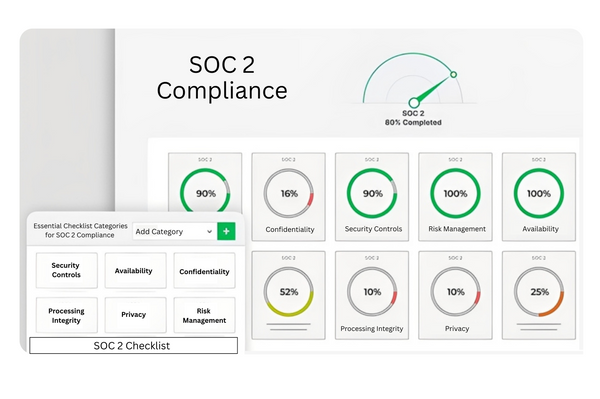
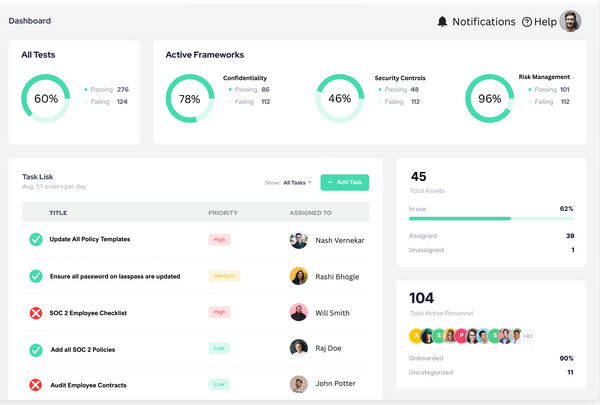
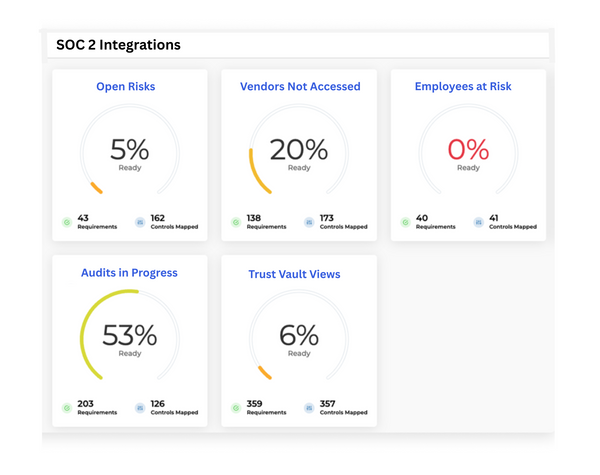
Want To Implement SOC 2 at Your Own Pace?
Take full control of your SOC 2 implementation with our easy-to-use DIY Toolkit. It includes step-by-step guidance, editable policy templates, and expert resources to help you achieve SOC 2 readiness independently.