ISO 27001 Patch Management and System Updates Policy Template
Introduction
Any effective Information Security Management System (ISMS) has a cornerstone strong ISO 27001 patch management policy, which is usually coupled with the system updates policy. The technical vulnerabilities management by the ISO 27001 standard is rather straightforward. For example, Annexe A.12.6.1 states that "all vulnerabilities of information systems must be evaluated and addressed through proper measures". In practical terms, this means keeping the software and operating systems up to date. Cybersecurity experts characterise patch management as the systematic process of identifying, testing, and deploying software updates to fix bugs and close security gaps. A specific patch management policy delineates how an organisation handles updates and monitors for compliance and risk reduction. Indeed, an ISO 27001 patch management policy is mandatory for certification. (Most teams initiate this work using templates for patch management policy.)
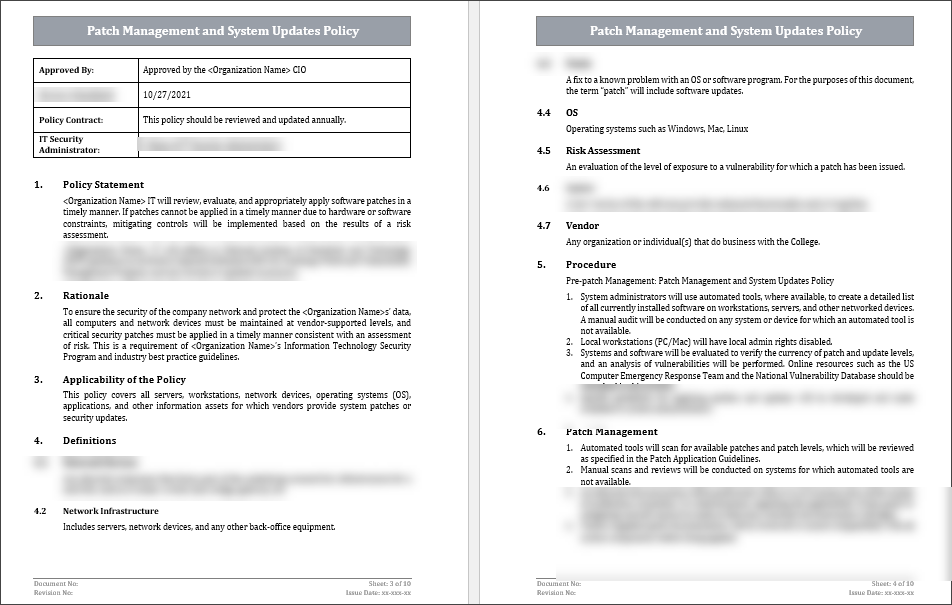
Importance of Patch Management Policy Template in ISO 27001
Subsequent to the patch management provisions under the ISO 27001 implementation standard for vulnerability management, systems need to be up to date for security and compliance with ISO 27001. The concept of vulnerability management entails proactively tackling technical vulnerabilities through maintaining asset inventories and applying patches in a timely manner, as set forth in ISO 27001 guidance under ISO 27002. In other words, unpatched systems are the most commonly used entry point for attackers to gain access. The updates and patches would thus close these entry points. Thus, patch management provides support for ISO 27001 because:
-
Remediation of Security Vulnerabilities: Software patches fix vulnerabilities known to security. An organisation closes off such exploitable flaws when it patches and updates its systems promptly, preventing the opportunity for attackers to exploit them.
-
Protection Against Newly Developed Threats: Cyber threats are continuously in the state of evolution. New attack techniques are created every other day, while unpatched software stands ever ready to offer an open invitation. With its updates, organisations, therefore, remain one step ahead of new threats and quickly deal with any new vulnerability that arises.
-
Preservation of Confidentiality, Integrity, and Availability (CIA): Cumulative patching preserves CIA for the information therein. Updates usually contain corrections for the integrity of any data and the availability of systems. In practical terms, it means that patched systems are stable and credible to authorised users.
-
Regulatory Compliance: Up-to-date systems are required by numerous statutes, standards, and contracts. Among them, ISO 27001 (clause A.12.6) prescribes that timely patching be an integral part of a resilient ISMS. Having an expressive policy amplifies the picture of compliance with many regulations (GDPR, HIPAA, NIST, PCI DSS) that require secure maintenance of their systems.
-
Strengthening Overall Security Posture: Regular patching is one of the many visible signs of a culture that espouses proactive security. Quick remedial actions for vulnerabilities are a declaration to management and stakeholders of the organisation's seriousness about security. This minimises the opportunities for breaches that tarnish reputation and incur losses.
- Preventing Inside Threats: Not all risks come from outside. As such, application updates also provide a shield against potential or questionable actions by insiders. Insider attacks, mistakes, or civil disturbances can all prove extremely damaging, particularly regarding unpatched systems, whereas patched systems close all chances.
In brief, the ISO 27001 patch management policy clearly articulates a schedule and procedure for these updates and patches. The policy addresses who will perform the patching, how patches will be tested and implemented, and how to respond to exceptions.
Key Elements of a Patch Management and System Updates Policy
An efficient software system update management program should be structured and detailed. Certain sections deserve more attention:
-
Document Control: Version, date, author/owner, classification. There must be a version-control system and assigned ownership for all policies as per ISO 27001.
-
Purpose/Objective: A policy exists for some reasons. For example, "The policy exists to ensure timely updating of operating systems, applications, and firmware for known security vulnerabilities."
-
Scope: What is being covered under this policy and by whom? It shall mostly apply to all employees and third parties and to all company IT assets covered under ISO 27001 (servers, workstations, network devices, applications, etc.).
-
Patching Procedures (Controls): Describes how patches are applied, which could be separated by asset type:
- For endpoints (workstations, laptops, and mobiles), use automated means (e.g. Windows Update Services, mobile MDM systems) for applying patches and regular checking (e.g. monthly scans) for keeping devices up to date.
- Patching for servers and production systems is usually done through a standard change management procedure, including testing processes (e.g. testing patches in a sandbox), scheduling maintenance windows, and fallback plans.
- For endpoints (workstations, laptops, and mobiles), use automated means (e.g. Windows Update Services, mobile MDM systems) for applying patches and regular checking (e.g. monthly scans) for keeping devices up to date.
-
Patch Classification and Response Times: How patches are prioritised. Many policies utilise severity ratings (Critical, High, Moderate, Low) along with deployment due dates. For instance, critical updates may be required to fix vulnerabilities allowing remote code execution "immediately," while the lower severity patches could then be deployed on the regular timeline.
-
Exceptions and Risk Management: Discuss the fate of the systems that cannot be patched. To this end, a list of exceptions should be maintained for any unpatchable system (e.g. obsolete hardware/software for which updates are not obtainable). Such exceptions should be inscribed within the organisation's risk register and handled in the risk treatment process: This will demonstrate to the auditor that one has recognised the risk involved and has an approved plan to manage it.
-
Monitoring and Compliance: Create a mechanism to ensure the timely review of patch status. For instance, make periodic vulnerability scans or compliance audits mandatory. Define how patch records are archived and punish any noncompliance. ISO 27001 demands that control is measured, and the outcome is further reviewed within the improvement mission.
- Communication and Training: Training on this policy will be given to all staff (for example, by posting it on the intranet), and employees will acknowledge having understood it. (It is also customary to ask staff members to sign their acknowledgement of this policy.)
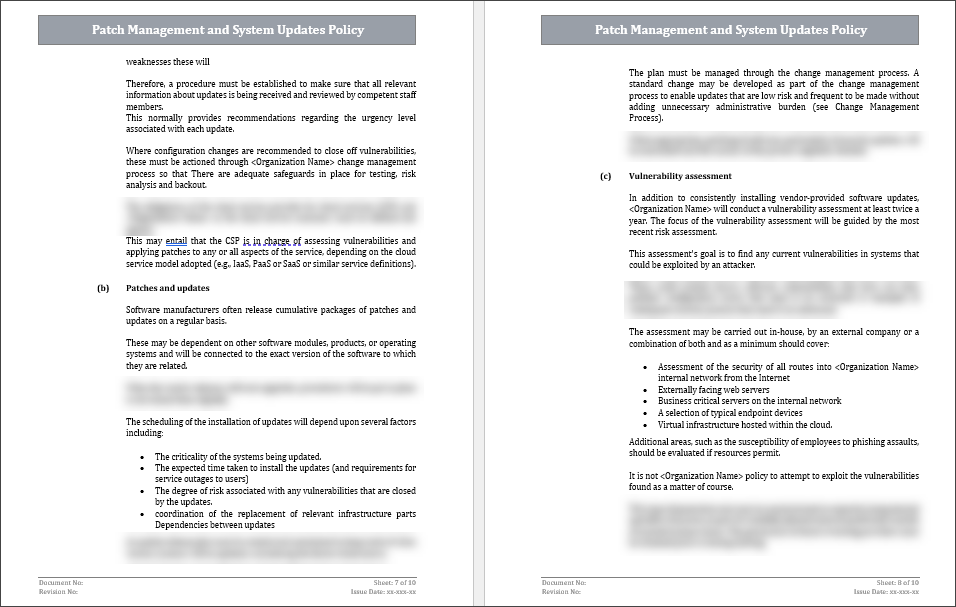
Patch Management Process and Best Practices
The policy is implemented through the structured patch management process, better known as the patch management lifecycle. The generic lifecycle is as follows:
-
Identify Vulnerabilities: Continuously look for new vulnerabilities. This may involve subscription to vendor security bulletins, automated scanning devices for scanning vulnerabilities, and a detailed, maintained asset inventory. (ISO 27002:2022 Control 8.8 states that asset lists be made and patches applied for discovered vulnerabilities as required.)
-
Patch Release and Prioritisation: After release of a patch (usually attached with release notes), it is reviewed by the IT department for relevance and then categorised according to severity/criticality. For example, emergency deployment is required for critical security patches concerned (e.g. a remote code execution fix). Less critical patches can be lined up during the next maintenance window.
-
Test Patches: Test patches within a controlled environment (especially for production systems) before wide deployment. This helps ensure compatibility and gets rid of unforeseen outages. Testing may use staging servers or virtual machines simulating a production environment.
-
Deploy Patches: Install patches approved according to priority. This might be automated (e.g. Windows WSUS/SCCM, Linux package management or mobile MDM) or manual. Critical patches might be deployed outside normal schedules immediately. Instead, the routine patches are deployed on planned maintenance windows to minimise user contact.
-
Verify and Report: Confirm and report success after patching, for instance, ensuring systems reboot and operate normally, and that scanners no longer report the vulnerability. Maintain logs of patches applied for audit evidence. If a patch has failed or caused problems, roll back or apply corrective measures and document the incident.
- Review and Adjust: Review patching regularly. It should ascertain that all critical patches were applied in a timely manner and that no impact on systems was missed. Find out any incident that was caused by a vulnerability that was not patched altogether. Analyse lessons learned to add value to the process (i.e. reducing time or updating testing procedures).
Best practices tend to contribute towards efficiency and security in this process, such as
-
Automate Wherever Possible: Thousands of endpoints can be administered by patch management tools. Applications are uniform, making errors less likely. For example, with automated patching on workstations and monthly compliance scans, any computers missing updates can be flagged quickly.
-
Segmentation: Core consideration of the network segmenting or testing zones. First, put the patches in place in a non-critical environment where you can monitor them for possible issues before rolling them into production.
-
Backup Before Patching: Always make sure to have recent backups or snapshots on call in case a patch brings with it some unexpected failure. This holds truer for servers or for critical devices.
-
Patch Categorisation: Clear definitions of patch categories. Most organisations use the common Microsoft severity qualifiers (roughly defined as Critical, Important, etc.) or OWASP ratings, while the policy will define expected response times, e.g. "Critical updates have to be applied within 24 hours, Important ones within 7 days," and so on.
-
Monitoring and Alerting: Establishment of a means to recognise absent patches. This may include IT asset inventory tools or vulnerability scanners, which give alerts if any known patches are missing. Provide visibility into this, along with combined management dashboards.
-
Change Management for Servers: Under a formalised change management process, integrate patch deployment into production systems. Change management defines how to schedule the patch under changes, obtain the requisite approvals, and notify interested stakeholders, which is in line with change management control of ISO 27001 (Annexe A.12.1.2).
- Exception Handling: Immediately record any patch that cannot be installed, for example, if incompatible software exists. Write the patch exception, the affected system, and the rationale in a risk register. Exception handling comes up periodically to see if incoming patches rectify the problem.
By keeping the patch life cycle simple and embracing all these good practices, organisations maintain admirable standards of software hygiene and substantiate due diligence as far as ISO 27001 is concerned. According to an industry guide, unpatched software becomes the front line target of attackers, hence effective patching "serves as a frontline defence against emerging threats.
Developing Your ISO 27001 Patch Management Policy
Yet, a few superior steps are at the core of creating a custom patch management policy. This is how I would propose the process:
-
Identify and Inventory Assets: Identify every ISMS hardware and software instance. This should include servers, desktops, laptops, mobile devices, and network devices, as well as critical applications. Document those items (vendor, product, version). An ISO 27001 requirement is an inventory of assets upon which the decision of what to patch will be based.
-
Prioritise by Risk: Rank the assets according to their importance and the sensitivity of data they handle. The focus should be on patching efforts on the highest-risk systems first (e.g., internet-facing servers; systems with confidential data). Such consolidation is done with risk.
-
State Purpose, Scope and Principles: Draft the statement of intent regarding the policy (e.g. "to ensure that all company systems are patched against security vulnerabilities in a timely manner"). Set up principles (e.g., "Update all software and hardware assets according to vendor instructions and best practices across the industry"). Clearly define the scope: "This policy applies to all employees, contracting parties, and systems owned or operated by [Company] in terms of implementation under ISO 27001.
-
Assign Roles and Responsibilities: Who would be held accountable for what? To quote: "The IT Director (or CISO) is responsible for the patch management program." A patch is worth monitoring by system administrators or IT support staff. End users must not disable automatic updates on their devices. Roles have to be put in writing so that they are accountable.
-
Exception Handling Process: Include how to manage those situations when a patch cannot be applied. State that all exceptions should be documented and that the system should be added to the organisation's risk register. For example: "When a patch cannot be implemented due to operational reasons, the information system will be classified as an exception and considered through the risk management process." This means that unpatched risks will be consciously managed by the auditors.
- Monitoring and Review: State how the policy will be kept effective; typically something like regular audits, inclusion in management-meeting reviews, or metrics (for example, percentage of systems patched on time). ISO 27001 requires ongoing improvement, and thus includes a commitment to review the policy at least annually or after major security events.
Conclusion
The Policy for the Conduct of Patch Management and System Updates in an ISO 27001-style should not just be a policy document; it must serve as a practical instrument to save the data and infrastructure of an organisation. Keeping the system updated in a regular and systematic manner closes the known security holes and thus minimises the risk considerably. A well-crafted policy that adequately addresses the requirements of ISO 27001 under Annexe A (such as A.12.6.1) defines the role of everyone involved in the patching effort.

