ISO 27001:2022 Cryptographic Controls Policy Template Download
Overview Of ISO 27001 And Its Place In ISMS Information Security Management System
ISO 27001 brings us to that international standard for risk management- ISO 270067: 2007; ISO/IEC 27001:2022 (or ISO 27001), to be followed by an array of its clauses by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). Internationally, this is the accepted international standard. All systematic procedures detailed in this document cater to enabling the corporation to establish, implement, maintain, utilize improvements, and perpetually advance the information security management system (ISMS) from its very founding steps. Lastly, ISO 27001 serves to uphold the Confidentiality, Integrity, and Availability (CIA) of information, regardless of the degree, size, or geographical distance of any organization.
Importance Of Cryptography Policy In ISO 27001 Related To ISMS: Introduction
ISO 27001 goes beyond stating that it offers international standardization medium most representative regarding information security management; even the more significant fact is that it recognizes its cryptographic policy to be weighed very significantly within an ISMS. This policy clarifies how the data are encrypted by unauthorized accessing or usage of the organization's sensitive information and therefore the confidentiality and security imparted to data. One of the strong implications of having an effectively-built cryptographic policy that organization has in its hands is the ability to be compliant and be represented in ISO 27001 and hence be secured against threats of cybercrime against their information. The reason cryptographic policy has importance in ISMS, define some best practices worth considering while setting up or maintaining a secure cryptography environment are the major points in this article.
It defines the control objectives of a risk-based management standard that develops activities and puts in controls to acknowledge and manage security threats to the information. These controls define the validity operational in a continuous review scheme. Considerations that include controls under this standard call for leadership support of the organization, stakeholder communication related to the organization, and continued improvements towards the objectives.
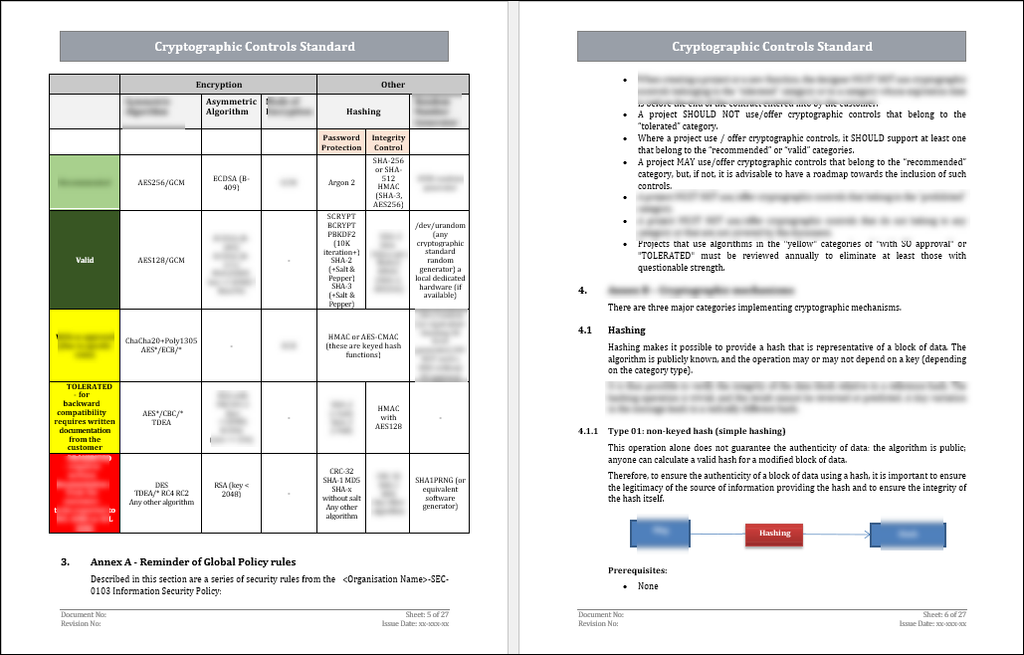
The very broadest possible area under which one can categorize control into ISMS will be cryptography-thus making use of the organization justified by proper policies and procedures for encrypting sensitive information and proper key management. Annex A control A.10 (now A.8.24-A.8.28 in ISO/IEC 27001:2022 Annex A) defines the principles of cryptographic policy comprising:
- Security of data at rest and in transit
- Secure management of cryptographic keys
- Selection of encryption algorithms according to risk exposure
- Protection of PII, financial data, and other sensitive data
Wherever cryptographic controls are tightly held, such denials will guard the organization's stronghold against unauthorized data access or theft occasioned by hackers in these days that have come under the eyes of more prying regulatory authorities and increasingly complex threats.
ISO 27001 is the one which adds ease to the integration with other management systems like ISO 9001 (Quality Management), ISO 22301 (Business Continuity), and ISO 27701 (Privacy Information Management). This integration would enable common governance across some business functions for these systems.
Nobody of course suggests that such compliance is merely a matter of regulation compliance (GDPR, HIPAA, and CCPA) but rather that it builds confidence with stakeholders by directing operations and resilience around a culture of security spread across the organization.
Strong Importance Of Cryptographic Policy Within The ISO 27001 Configuration Framework
Basic policies will constitute around cryptography controls for the definition of sensitive data needing protection in this day of free flow of data, thus creating an organization that is crucial to its business. Cryptographic controls protecting sensitive data under ISMS is an art and science within the framework of ISO/IEC 27001:2022. The importance of this can be conferred for several reasons:
1. Protecting Sensitive Data
Encryption-at-rest-and-in-transit often proves to be one of the best ways to avoid tampering with sensitive information. It ensures that:
- All files, databases, and channels for communication are duly encrypted.
- Sensitive data might, at established times and conditions, be accessed or decrypted by the authorized only.
2. Lessens Risk of Data Breaches
Your organization essentially lowers the risk that unauthorized users or parties can exercise access and limit damages upon the possible exposure of sensitive data or disruption events that might arise as a result of data breach incidents or system compromise activities by means of strong encryption standards and key management practices.
3. Supports ISO 27001 Compliance
The existence of a cryptographic policy that satisfies a number of controls regarding cryptography listed in Annex A (from A.8.24 to A.8.28 of the standard) assures that its implementation would:
- Rely on risk assessment and be proportionate to its implementation on encryption across your organization
- Accept and accurately document requirements related to secrecy, integrity, and availability for protection of information.
4. Empowers Your ISMS Base
A cryptography policy cannot be defined in isolation; it has to be seen in the context of the wider ISMS. The implementation of:
- Risk assessment (to identify the areas where encryption is needed)
- Access control and identity verification
- Data classification and diffusion protection strategies
5. Builds Trust with Stakeholders.
Clients, partners, and regulators could be reassured that your organization indeed cares about data protection, towards which a well-implemented cryptographic policy:
- Exhibits security posture in a proactive manner
- Develops trust in your brand and business operations
6. Preparing You for Changing Threat Increases
These cryptography threats and technologies change fast; a strong policy will:
- Call for periodic review and update of the encryption algorithm
- Ensures that by changes in security standards, the organization could adapt even faster in this case.
7. Encourages security-minded Culture
Not just around technology but very much about people as well. Your cryptographic policy should:
- Include awareness training so that staff understand their role in data protection
- Encourage secure practice in daily operations such as handling encrypted files or using VPNs.
Major Elements Of A Cryptographic Policy
To write a cryptographic policy that adequately protects your organization requires more than just an encryption method definition; it builds a fortified, systematic framework for the design, application, and maintenance of encryption. The basic components that lead to the being both effective and ISO/IEC 27001 compliant are:
1. Strong Encryption Standards
- Make use of accepted encryption standards (e.g. AES-256, RSA, SHA-256).• Encryption should be applied against both data at rest (e.g. databases, file servers) and data in transit (e.g. messages, network traffic).
- Stop using deprecated and weak algorithms (e.g. MD5, DES) that are no longer considered safe.
2. Secure Key Management
- Define the ways in which cryptographic keys are generated, stored, used, rotated, and destroyed.
- Policies regarding key lengths, expiration, and renewal cycles must be implemented.
- There must be a clear segregation of roles between key management and key usage.
3. Protect Cryptographic Keys
- Store keys in secure locations such as Hardware Security Modules (HSMs) or encrypted key vaults.
- Limit access to keys on the basis of roles and responsibilities.
- Conduct access monitoring and review access logs for unusual activities in the use of keys.
4. Data Integrity
- Protect the integrity of data during transmission/storage through the use of digital signatures, checksums, or hash functions.
- Build trust mechanisms for data authenticity and integrity.
5. Policy Alignment with ISO 27001 Standards
- Make sure that cryptographic practices are aligned with ISO 27001 Annex A controls (A.8.24 to A.8.28).
- Integrate cryptographic policy with overall ISMS such as risk assessments, access control, and business continuity plan.
6. User Awareness and Training
- Train employees to understand the functioning of encryption tools and how to handle encrypted data.
- Security awareness programs should address key points of cryptography.
7. Ongoing Review and Improvement
- Monitoring cryptographic protocols and algorithms will ensure they remain relevant against evolving threats and industry standards.
- The policy should vary as per the results of audits, vulnerabilities assessed, or context-change in technology.
Implementation Steps For Developing And Enforcing A Cryptographic Policy
The development of a cryptographic policy extends beyond the confines of forming and implementation; rather, a system is to be built wherein sensitive information is protected, wherein security is guaranteed, and which is compliant with ISO 27001. This article provides a step-by-step practical approach in developing and enforcing an organization-wide cryptographic policy:
1. Risk Assessment Should Be the Starting Point
- Look for an area where sensitive information resides, is processed, and transmitted through.
- Identify possible threats of data interception, unauthorized access, or tampering.
2. Identification of Encryptable Items
- Document specific types of data that are subject to encryption: this specification could be all PII, financial records, login credentials, etc.
- Encapsulation of data transmission (email, web traffic) and data storage (databases, backup).
- Include third-party, mobile, and cloud-based data.
3. Appropriate Encryption Standards Must Be Selected
- Select encryption algorithms and key lengths recognized in standard (AES-256, RSA 2048+).
- Do not approve extremely outdated or weak algorithms (MD5, DES).
- Consider speed, compatibility, and regulatory authorities.
4. Secure Key Management Procedures Must Be Established
- Define procedures for generation, storage, distribution, rotation, and destruction of keys.
- Keys must be stored in a secure hardware vault (HSM or equivalent).
- Duties and access controls on handling keys must be enforced.
5. Integrating Cryptographic Controls into Daily Operations
- Include encryption into access control, back up, or transfer of data processes.
- Ensure system and application automatic use of encryption.
- Consistent with other ISMS policies like data classification, asset management, and business continuity.
6. Training and Awareness of Staff
- Training on the handling of encrypted data and the reason it matters.
- Ensure that employees can recognize secure file formats and the correct use of encryption tools.
- Include cryptography awareness in onboarding and refresher programs.
7. Monitoring, Auditing, and Reviewing
- Regular audits should be conducted for the assessment of enforcement toward cryptographic policies.
- Audit logging should be used to flag suspicions of unauthorized activity through automated alerts.
- Regular reviews and amendments of the cryptographic policy should follow an audit recommendation along with newly discovered threats or regulatory changes.
Common Pitfalls To Avoid When Defining Cryptographic Policies Per ISO 27001
Drafting a cryptographic policy in compliance with ISO/IEC 27001 is not merely a mechanical process but an occasion for the real and effective decisions on security to be made. Nevertheless, organizations, with the right intentions, often fall into a few common traps. Here are those to look out for:
1. Failing to Consider Encryption for All Sensitive Data
- Many organizations encrypt some classes of data and neglect others, especially data at rest such as files stored on laptops or, more importantly, databases.
- Data in transit—be it an email, web traffic, or API calls—should never be neglected as it is as susceptible.
2. Use of Deprecated or Weakened Encryption Algorithms
- This puts your data at risk with generic encryption like MD5, SHA-1, or 3DES.
- These algorithms are no longer secure against attacks from current hackers.
3. Disastrous Key Management
- A red flag for sure would be the storage of cryptographic keys in spreadsheets, emails, or unsecured file shares.
- Lack of procedures for the generation, rotation, and destruction of keys is an avenue for serious vulnerabilities.
4. Non-Documentation of Cryptographic Controls
- Without the documentation of all processes involving the encryption policy template mechanisms, key management tools, and related policies, auditing them will be tough, if not impossible.
- Lack of proper documentation can lead to differences in opinion and setup from one department or team to another.
5. Ignoring the Evolution of Threats
- What was secure two years ago may not be today.
- Allowing the "set it and forget it" attitude will soon result in new vulnerabilities.
6. Overcomplicating the Policy
- At times, the policy is difficult to implement since it is either too technical or too full of jargon.
- If it is too complex to be utilized, most likely, people will label it as unusable, put it on the shelf, and forget about it.
7. Policy Enforcement Lacks Consistency
- To have gaps, apply cryptographic controls in one department and not the others.
- Without uniform enforcement, the organization may be riddled with exploitable gaps.
Conclusion
To wrap up, ISO 27001-compliant cryptographic practices are paramount to the great information security efforts of organizations. These common pitfalls can be addressed with robust cryptographic policies; hence organizations may secure sensitive information. Key in cementing security frameworks is to encrypt data at rest and in transit and keep scrupulous documentation of processes and cryptography while keeping abreast of encryption standards. The consistent monitoring of threats embraced by such comprehensive cryptographic policies sets the pace. Ultimately, organizations’ priorities in secure cryptographic practices based on the ISO 27001 standards can shield them from cyber threats and their trusted assets.

