ISO 27001 Checklist Template for Requirements
The ISO 27001 Requirements Checklist is a document that provides an overview of the requirements for securing information. It is designed to be used by managers, security professionals, and auditors responsible for implementing the controls specified in ISO 27001. The checklist helps you identify areas where you may need to apply additional measures or revisit existing controls.

This checklist covers the basics of what you need to know about ISO 27001 Requirements Checklist.
- You should have an information security policy in place before starting the implementation process for this checklist. The policy will guide your decisions and help you determine how much effort you want to put into implementing each requirement on the list.
- There are 12 requirements that are considered “mandatory” by ISO standards, meaning they must be met or risk not being able to certify as meeting ISO 27001 requirements at all (which would make it difficult for companies who use compliance with this standard).
ISO 27001 is an international standard that provides guidance on how to develop, implement, operate, and maintain information security management systems.
The ISO 27001 requirements checklist includes 26 items that are organized into the following six categories:
1) Information Security Policy
2) Organization of Information Security
3) Asset Management
4) Human Resources Security
5) Physical and Environmental Protection
6) Communications and Operation Management
Why is an ISO 27001 Checklist Important?
ISO 27001 is a security management standard that helps organizations to protect their information assets and reduce the risk of data loss. The standard provides guidance on how to manage risks and controls for protecting information assets, as well as the process of maintaining these standards and controls over time.
When implemented correctly, organizations that follow these guidelines have seen a number of benefits including better information security management practices; improved risk assessment methods; strengthened customer trust due to increased transparency regarding confidentiality of their data; faster response time for dealing with data breaches or other incidents involving personal information which helps avoid damage from reputational harm.
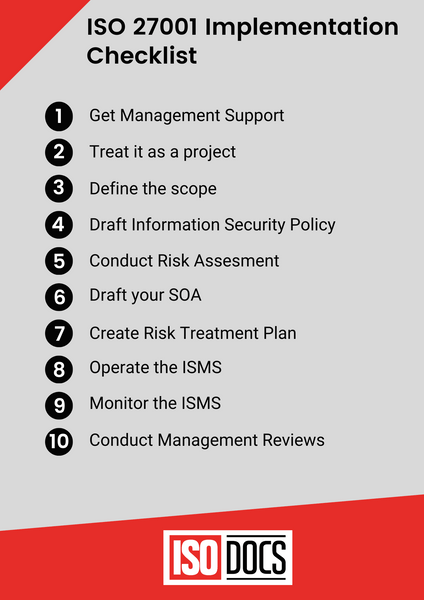
ISO 27001 Checklist: Steps for Implementation
1. Management Support
When implementing ISO 27001, it is important to have strong management support. Management buy-in will help the implementation be successful. Here are some tips on how to get your managers on board with an ISO 27001 implementation:
- Be articulate and knowledgeable about the benefits of compliance as well as the risks of non-compliance.
- Identify a person within your organization who can assist in making decisions and providing guidance.
- Inform all levels of management about what you’ve been doing throughout each phase or step in the process, from planning to implementation and beyond.
- Create a plan for moving forward and make sure you follow it.
- Set up an open line of communication between yourself, management, and other relevant parties to ensure everyone is aware of the steps being taken to implement ISO 27001. This will help remove any barriers or obstacles that may be in your way as well as demonstrate how compliance can benefit all levels within the organization.
2. Treat it as a Project
The ISO 27001 checklist is a list of actions that need to be taken in order for an organization to be compliant with the ISO 27001 standard. There are many different standards and regulations designed for specific industries, so it’s important to know what you’re dealing with before you start your project. The first thing on the checklist is “identify requirements.” This means gathering all relevant information about the policies, laws, regulations, industry standards, etc., that apply to this project.
3. Define the Scope
ISO 27001 is a set of standards that are focused on information security. It was created by the International Organization for Standardization (ISO) in order to provide organizations with guidance on how they can maintain their data and physical assets securely.
The ISO 27000 series consists of seven management systems, one of which is called “Information Security Management System.” This system has five main components: Asset identification, Risk assessment, Control implementation, Information Security policy statement and Awareness training. One thing that you need to do before implementing this system is to define the scope. Defining the scope means determining what needs to be protected or secured within your organization’s broader strategy. You will also need to identify any other parties that could be impacted by your decisions regarding information security.
4. Information Security Policy
The purpose of an Information Security Policy is to provide a framework for managing information security risks. A policy defines the organization’s expectations for how people are expected to behave when using information systems and also defines what happens if those expectations are not met. The most important component of any policy is the implementation plan that covers who will be responsible for ensuring compliance with the policy.
- Information Security Policies need to be tailored to meet your organization’s needs – there is no one-size-fits-all solution that can cover every possible situation or requirement. You should consider what information you want to be protected, which types of attacks you are vulnerable to, and whether employees have access only locally or over a network as these factors determine what type of policies might be needed.
- Another part of the policy will be how to communicate with employees about security protocols in place and encouraging them to understand why these policies are being put into place. If you have your own training program, this is where it can be included within the Information Security Policy so that everyone has access to any resources they might need when required.
5. The Risk Assessment Methodology
The risk assessment methodology in ISO 27001 Checklist is a systematic process of identifying the possible risks to an organization’s security and then determining how best to mitigate them. It involves four steps:
Step 1 – Identify what you are trying to protect
Step 2 – Establish the objectives for protection
Step 3 – Assess vulnerabilities
Step 4 – Evaluate risks.
6. Perform the Risk Assessment & Risk Treatment
Risk assessment is an important step in ISO 27001 information security management and should be performed before the risk treatment. Some things to consider when performing a risk assessment are:
1) Identify all risks that might affect the company’s objectives.
2) Determine if any of these risks are likely to occur within a specific time period.
3) Evaluate how severe each identified risk is based on probability and impact.
4) Assess tolerance for each identified risk. Once you have completed your risk assessment, you will know what areas need more attention or additional protection.
7. Statement of Applicability
Statement of Applicability is a measure that defines the scope and applicability of an organization’s system security measures. The Statement of Applicability (SOA) will contain:
- The organizational profile.
- Principles governing the design and operation of information systems, including risk management.
- Criteria for selecting suppliers from which it acquires products or services with security significance to its information systems.
- Roles and responsibilities in implementing SOA requirements.

8.Risk Treatment Plan
The Risk Treatment plan is an important part of the ISO 27001 Checklist.
- It helps to identify, assess, and control risks that could affect the confidentiality, integrity, and availability of information assets.
- Risks are identified through a process of considering potential consequences that might occur if they were realized. The risk treatment plan includes controls to reduce or eliminate these risks as well as contingency plans in case they do happen.
9.Operate the ISMS
Operate the ISMS in ISO 27001 Checklist is one of the most important parts of an Information Security Management System. It sets out how to operate your ISMS and helps you manage risks, controls, and security incidents effectively.
The checklist consists of four main sections: Planning for an Information Security Program; Developing Policies, Procedures, Standards, Guidelines and Documentation; Implementing Controls; Measuring Performance Metrics.
10.Monitor the ISMS
ISO 27001 is a standard that outlines how to monitor the Information Security Management System (ISMS). The checklist below will help you when implementing ISO 27001 in your organization. It includes all of the steps and procedures needed for a successful implementation of an ISMS.
- Step 1: Define what needs to be monitored within the scope of your organization’s ISMS by considering risks, vulnerabilities, threats, and impacts resulting from not meeting standards. This step should include assigning responsibility for monitoring each item to one individual or group who will work with other stakeholders on this task.
- Step 2: Develop a plan for how these items will be monitored using existing resources such as policies, guidelines or standards that are already in place. You will also need to consider any additional resources that may be needed.
10.Internal Audit Plan
The Internal Audit Plan in ISO 27001 Checklist is a document that describes the audit process and its objectives. It also defines how to carry out an audit, which includes the scope of the audit, what information to collect during audits, and who should conduct audits. The plan establishes a clear understanding of how auditors will perform their work and provides guidelines for managing risks associated with system security.







